- Azure Application Gateways provide a reverse proxy Layer 7 load balancer solution in Microsoft Azure. From a PaaS point of view, they’re very handy, providing full Azure integration for deploying through ARM, PowerShell and CLI.
- AD FS provides simplified, secured identity federation and Web single sign-on (SSO) capabilities. Federation with Azure AD enables users to authenticate using on-premises credentials and access all resources in cloud. As a result, it becomes important to have a highly available AD FS infrastructure to ensure access to resources both on-premises and in the cloud.
- The option to add custom headers to the Azure Application Gateway, so we can use the Application Gateway as a reverse proxy The option to add custom headers, so we can use the Azure Application Gateway as a reverse proxy for e.g. ADFS needs two headers to be set: 1.
We are converting a ASP.NET Web Application to Azure. The Authentication process is handled using LDAP call in the existing code, but we are planning for ADFS integration. The ADFS server already exposing the claims to Microsoft Federation Gateway to consume by other applications.
Website Documentation for your KeePass client and Pleasant Password Server
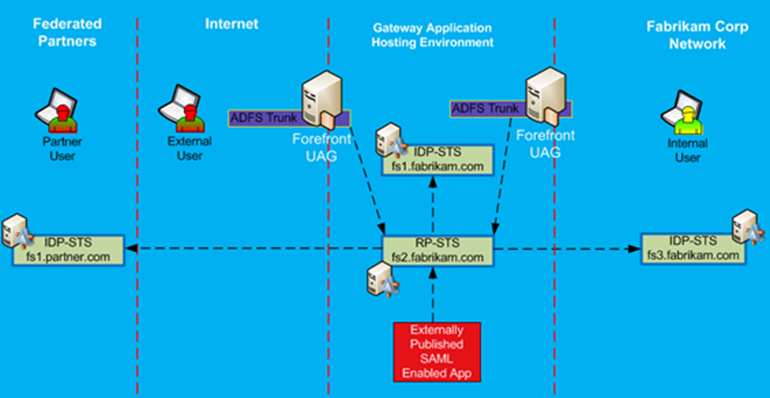
The following steps can be used to setup an configure SAML SSO with Azure AD.
This will allow your users to be authenticated onceusing Azure credentials and not be prompted again if they are already signed in.
Applies to: Versions 7.9.9+, Enterprise+SSO
Related (similar configuration steps):
Pre-Requirement:
- Install & register Password Server Enterprise+SSO
- Import AD/LDAP Directory users
Please Note:
- These steps are still a work in progress. Contact us if you have questions
Setup Overview

The following steps can be used to setup an configure SAML SSO with Azure AD.
This will allow your users to be authenticated onceusing Azure credentials and not be prompted again if they are already signed in.
Applies to: Versions 7.9.9+, Enterprise+SSO
Related (similar configuration steps):
Pre-Requirement:
- Install & register Password Server Enterprise+SSO
- Import AD/LDAP Directory users
Please Note:
- These steps are still a work in progress. Contact us if you have questions
Setup Overview
- Step 1 - Configure SAML in Pleasant Password Server
- Step 2 - Add a new App in Azure AD
- Step 3 - Configure the Single Sign-On Method
- Step 4 - Configure a new SAML Partner
- Step 5 - Assign Group to the new App
Step 1 - Configure SAML in Pleasant Password Server
Open the Authentication Services configuration page from the Users & Roles menu.
- Click Add SAML Configuration
Provide an Issuer Name value
- This value identifies your Pleasant Password Server application to the Identity Provider (Azure AD)
- e.g. PasswordServer
- 'Issuer Name' = Azure AD Identifier (Entity ID)
- Suggestion: Do not use any spaces when typing the 'Issuer Name'
- This value identifies your Pleasant Password Server application to the Identity Provider (Azure AD)
(optional) Provide a certificate for digitally signing SAML requests and responses
- Single Log Out (SLO) on Azure requires that the requests be signed
- See the certificate section for instructions on creating and configuring a signing certificate
Note: only .pfx or .p12 formats are accepted currently. Use the steps mentioned here to convert (Option A, step 2).
- This certificate can be a self-signed certificate for Azure
- The Azure provided certificate may need to be downloaded and setup on the Password Server machine as a trusted certificate
- Be sure that your IIS user account (or AppPool) has read permissions to the imported certificate
Save the configuration
- Copy the values for Issuer Name, Assertion Consumer Service URL, and Single Log Out Service URL
- Assertion Consumer Service URL = Reply URL (needed in the new Azure AD Enterprise Application)
- If using a certificate for signing you will also need to export the public key
- Note: only .pfx or .p12 format is accepted currently. Use the steps mentioned here to convert if needed.
- If the URLs are directed to localhost, but this is not the URL you intend to use then you should sign in via that URL first
Step 2 - Add a new App in Azure AD
Follow these Azure configuration steps which appear to best document the process from this Microsoft Guide:
- Create a new 'Non-gallery application'
- Use a convenient name
Step 3 - Configure the Single Sign-On Method
Azure Web Application Gateway
- Open the new App and click on 'Single Sign-On'
- Select SAML protocol
- Use the 'Identifier (Entity ID)' as 'Issuer Name'
- Paste the reply URL and then Save
- Write down the 'Azure AD Identifier' and the 'Login URL'
Create Application Gateway Azure
Step 4 - Configure a new SAML Partner
- Add a new SAML Partner Configuration from the 'Authentication Services' in Pleasant Password Server
- Paste the 'Azure AD Identifier' as Name
Example: https://sts.window.net/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/
Use a friendly display name to identify service
- Example: Azure SSO
Click on 'Single Sign-on' tab
Enter the Service URL
- Example: https://login.microsoftonline.com/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/
Click on 'Single Sign-out' tab
- You must have followed the optional steps in parts 1 and 2 to configure Single Log Out
- Enter the same value for Service URL as you did for Single Sign On
Example: https://login.microsoftonline.com/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/
- Leave Service Response URL blank
- Select Post as the Binding Method
- Check both Sign Log Out Request and Sign Log Out Response
Save Configuration
Part 5 - Restrict SSO Login (Optional)
- Option to restrict sign-in with your trusted Identity Provider, and only allow sign-in locally in the case of emergencies by admins:
- seeRestricting SSO Logins
Step 6 - Assign Group to the new App
- Add federated group 'Pleasant Password Users' as User of the new App
- Test connection from Pleasant Password Server
- Review Sign-in Activity from the Azure AD Portal
References:
Troubleshooting
